3G (third generation of mobile telephony)
What is 3G (third generation of mobile telephony)?
3G refers to the third generation of cellular technology that enables mobile telephony. The third-generation standard follows two earlier generations that were deployed on mobile networks and across mobile phones.
The International Telecommunication Union (ITU) defined the third generation of mobile telephony standards International Mobile Telecommunications 2000 (IMT-2000) to facilitate growth, increase bandwidth and support more diverse applications. For example, Global System for Mobile Communications (GSM) technologies could deliver not only voice, but also circuit-switched data across mobile phone networks at speeds up to 14.4 kilobits per second (Kbps). To support mobile multimedia applications, however, the 3G standard had to deliver packet-switched data with better spectral efficiency at far greater speeds.
History of mobile telephony
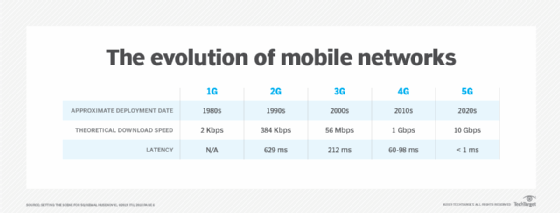
The first-generation (1G) standard got its start in the early '80s with commercial deployment of Advanced Mobile Phone Service (AMPS) cellular networks by network providers. Early AMPS networks used frequency division multiple access (FDMA) to carry analog voice over channels in the 800 megahertz (MHz) frequency band across radio access technology.
The second-generation (2G) standard emerged in the '90s when mobile operators deployed two competing digital voice standards. In North America, some operators adopted Interim Standard 95 (IS-95), which used code division multiple access (CDMA) technologies to multiplex up to 64 calls per channel in the 800 MHz band. Across the world, many operators adopted the GSM standard, which used time division multiple access (TDMA) to multiplex up to eight calls per channel in the 900 and 1,800 MHz bands.
To get from the 2G to the 3G standard, mobile operators had to upgrade existing networks while planning new mobile broadband networks. This led to the establishment of two distinct 3G families: 3GPP and 3GPP2.
The 3rd Generation Partnership Project (3GPP) was formed in 1998 to foster deployment of 3G networks that descended from GSM. 3GPP technologies evolved as follows:
- General Packet Radio Service (GPRS) offered speeds up to 114 Kbps.
- Enhanced Data Rates for Global Evolution (EDGE) reached up to 384 Kbps.
- Universal Mobile Telecommunications System (UMTS) Wideband CDMA (WCDMA) offered downlink speeds up to 1.92 megabits per second (Mbps).
- High-Speed Downlink Packet Access (HSDPA) boosted the downlink to 14 Mbps.
- Long-Term Evolution (LTE) -- or Evolved Universal Terrestrial Radio Access (E-UTRA) -- aimed for 100 Mbps.
GPRS deployments began in 2000, followed by EDGE in 2003. While these technologies are defined by IMT-2000, they are sometimes called 2.5G because they did not offer multimegabit data rates. EDGE was superseded by HSDPA and its uplink partner, HSUPA. According to 3GPP, there were 166 HSDPA networks in 75 countries at the end of 2007. The next step for GSM operators, E-UTRA, was based on specifications completed in late 2008.
A second organization, 3rd Generation Partnership Project 2 (3GPP2), was formed to help North American and Asian operators using CDMA2000 transition to 3G. 3GPP2 technologies evolved as follows:
- Single-Carrier Radio Transmission Technology (1xRTT) offered speeds up to 144 Kbps.
- Evolution-Data Optimized (EV-DO) increased downlink speeds up to 2.4 Mbps.
- EV-DO Revision A (Rev. A) boosted downlink peak speed to 3.1 Mbps and reduced latency.
- EV-DO Revision B (Rev. B) can use two to 15 channels, with each downlink peaking at 4.9 Mbps.
- Ultra Mobile Broadband (UMB) reached 288 Mbps on the downlink.
1xRTT became available in 2002, followed by commercial EV-DO Release 0 in 2004. Here again, 1xRTT is referred to as 2.5G because it served as a transitional step to EV-DO.
EV-DO standards were extended twice. Rev. A services emerged in 2006 and were succeeded by products that use Rev. B to increase data rates by transmitting over multiple channels. 3GPP2's next-generation technology, UMB, did not catch on, as many CDMA mobile phone network operators moved to LTE instead.
LTE evolved to become a core component of the fourth-generation (4G) wireless technology standard, providing a higher peak data transfer rate than 3G. The 4G standard can provide up to 100 Mbps downstream and up to 30 Mbps of upstream bandwidth capability. Mobile operators first deployed 4G in 2009.
4G has since been superseded by the fifth-generation (5G) wireless standard, which began deployment in 2019. 5G technologies offer even higher peak speeds than 4G, with a theoretical peak speed that can reach up to 20 gigabits per second (Gbps).
Areas of application
There are a number of use cases and applications for 3G technologies:
- Mobile networks. The 3G standard is most commonly used within mobile networks and their radio access technology platforms.
- Mobile phones/smartphones. The most common 3G devices are mobile phones for basic voice and text connectivity, as well as smartphones that provide more capabilities to users for data transfer and access. 3G-enabled smartphones helped drive development and adoption of mobile internet sites.
- Mobile broadband routers. For both consumer and business use cases, mobile broadband routers that support the 3G standard can enable internet connectivity for endpoint devices that are attached to the router -- either via a wire or Wi-Fi.
- Computer modems. 3G Universal Serial Bus (USB) modems for computer laptops enable cellular connectivity for devices that don't have access to Wi-Fi or a wired network connection.
- Cellular backup. In various devices -- including wired routers and home alarm systems -- a cellular backup option is sometimes available. Cellular backup enables the primary connectivity via a fixed wired connection, and in the event of a failure, the device will fail over to use the cellular connection.
- Telematics. 3G is widely deployed to enable telematics applications for the automotive industry, enabling vehicles to share information for transportation and fleet management use cases.
Differences among 3G, 4G and 5G
There are a number of key differences across the 3G, 4G and 5G standards. The most basic and primary difference is that each successive generation offers the promise of an increased peak speed. However, speed isn't the only differentiator as access technology also changes in each platform, requiring mobile phone network providers and mobile phone users to upgrade devices and radio access technology.
- 3G provides a peak speed of up to 14 Mbps and works at frequencies up to 2.1 gigahertz (GHz).
- 4G has a peak speed of up to 100 Mbps and works at frequencies up to 2.5 GHz. 4G technology includes multiple input, multiple output (MIMO) and orthogonal frequency-division multiplexing (OFDM) technologies to increase speed and capacity over 3G.
- 5G has a theoretical peak speed of 20 Gbps and works at frequencies of up to 95 GHz. 5G also offers the promise of reduced power consumption over its predecessor, which will enable more use cases, including embedded deployment for internet of things (IoT) devices.
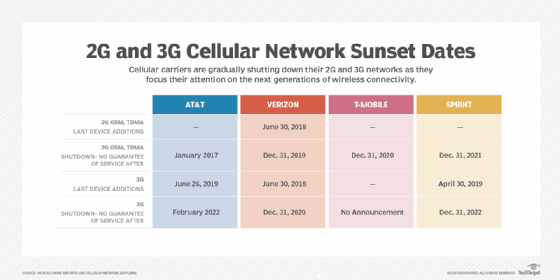
2G and 3G cellular network sunset
While there has been a degree of backward compatibility across cellular network standards, enabling newer smartphones to run on mobile phone networks that support older standards, network providers around the world are moving to decommission the older 2G and 3G networks. The move is intended to help advance the adoption of newer standards and optimize radio access technology platform deployments that mobile phone network operators need to support.