
Rawpixel - Fotolia
VoIP migration requires telephony network planning, security scrutiny
A PBX to VoIP migration requires careful planning to ensure call quality. Learn how to ready the network, evaluate architecture options and set the right security policies.
Organizations that want to modernize their telephony services and scrap old PBX systems are migrating to voice over IP. But a VoIP migration requires significant planning, from preparing the corporate LAN for voice traffic to setting security policies to protect call data.
Whether completely overhauling your telephony infrastructure or taking a more gradual approach, learn how to prepare your network for VoIP and keep your services secure.
How do I prepare my network for VoIP?
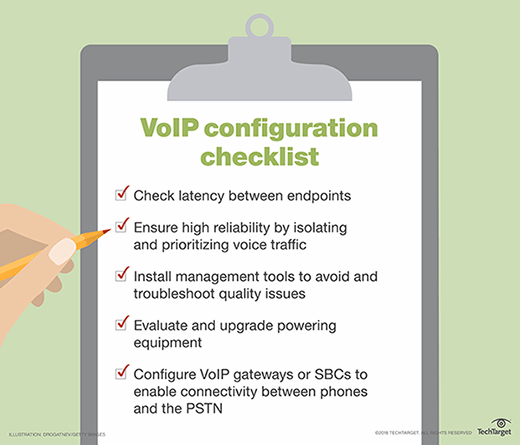
Before migrating to VoIP, organizations need to evaluate several infrastructure considerations. Most important is access to the public-switched telephone network (PSTN). All calls outside of a company require access to the PSTN. VoIP gateways are needed to translate the data between legacy telecom networks and the corporate LAN. Organizations can also deploy session initiation protocol (SIP) trunking to transport voice directly to the PSTN carrier.
Organizations must also prepare the LAN for VoIP to ensure voice calls have enough end-to-end throughput with limited latency and jitter. IT should audit critical network uplinks across the LAN to identify potential areas of congestion. IT should also configure end-to-end quality of service (QoS) policies to ensure voice calls maintain priority on the network.
Endpoints, such as desk phones and softphones, are also important network factors to consider. For desk phones, organizations must address how phones receive power. Most VoIP phones don't receive power from the phone network, like analog phones, and require an external power source, such as Power over Ethernet. Organizations that deploy softphones as part of a VoIP migration must ensure wireless LAN access points can prioritize voice traffic and have enough coverage to avoid dead spots and bottlenecks.
How does hybrid factor into a VoIP migration?
Some organizations may opt for a hybrid VoIP deployment to take a more phased migration approach. Organizations can tackle a hybrid migration in several ways. For example, they could migrate low-priority outbound calling to VoIP to test the service's performance and iron out issues before they affect important calls, such as inbound calls to contact centers. Organizations can use a hybrid deployment as a test environment to emulate network degradation and measure VoIP quality and performance.
Organizations can also use a hybrid VoIP migration as a stepping stone to unified communications as a service (UCaaS). This type of deployment would use the legacy system as the phone system's foundation and add VoIP capabilities on top of it. Users could keep their existing analog handsets and place calls over an IP network. A hybrid VoIP deployment would also allow organizations to maintain advanced telephony features that may not be available in a UCaaS system.
How do I keep my VoIP service secure?
Security is an important aspect of a VoIP migration as IP-based calling is vulnerable to several threats. Denial-of-service (DoS) attacks are the most common threats, where a phone system is flooded with illegitimate traffic to prevent users from sending or receiving legitimate calls.
A good firewall, either provided by the VoIP vendor or a third party, can mitigate DoS attacks. Additionally, session border controllers (SBCs) can protect against DoS attacks. SBCs serve as a firewall for voice traffic by applying their own QoS policies and identifying incoming threats.
Call jacking and man-in-the-middle attacks can occur when SIP traffic is intercepted and a malicious actor can eavesdrop on conversations and capture sensitive information. These types of attacks can be prevented by using VPNs and encryption. Softphones should also have antivirus and antimalware software installed.
Evil twin attacks occur when a wireless access point is copied to phish for information. VoIP users who log in on an evil twin access point compromise their credentials and information shared over calls. Softphones compromised by an evil twin are at risk of spoofing and call fraud. Organizations can mitigate evil twin attacks by encrypting wireless networks and using VPNs.







