
Rymden - stock.adobe.com
Top hybrid collaboration security threats and strategies
Hybrid work can add new security wrinkles for collaboration tools. Learn about the key threats and the importance of a proactive hybrid collaboration security strategy.
As organizations return to office environments and establish hybrid workplaces, employee collaboration tools and services take on added meaning. How organizations secure those services and their users across home and corporate networks becomes increasingly important.
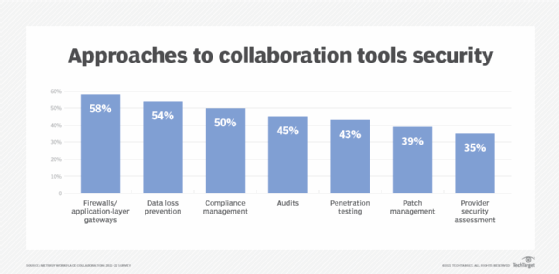
Although collaboration security is a top priority for many businesses, only 40% of organizations have a proactive security plan, according to a recent Metrigy study. Collaboration security is "not quite where it needs to be," said Metrigy analyst Irwin Lazar.
Recently, a high-profile breach highlighted the need for proactive hybrid collaboration security plans. Video game publisher Electronic Arts (EA) experienced a data breach in which hackers stole and reportedly sold proprietary game source code and development tools.
The hackers breached EA's corporate network by fraudulently accessing a Slack channel. Once in the channel, the hackers messaged EA's IT support team and received authentication to access the corporate network.
With collaboration security, most companies are in reactive mode, Lazar said. The first step in a proactive security plan is to figure out what is at risk and how to secure those risks. Organizations should evaluate risks based on their industry and determine their tolerance for risk, he said.

Hybrid collaboration threats to consider
Unauthorized access to meetings, which was a top concern earlier in the COVID-19 pandemic, is still a security threat. However, most organizations are now better about requiring video security features like waiting rooms and user identification, Lazar said.
For team collaboration, the main priority is managing guest access, Lazar said. This includes setting up a team space, inviting a guest user and determining when to revoke access. Organizations also need to decide if guest access or federation is the better option to connect external users.
Since team collaboration workspaces are persistent, organizations need to set policies on monitoring sensitive information, how long channels should be active and ensuring users can't make changes to workspaces without IT's knowledge, said Devin Redmond, CEO of Theta Lake, a collaboration compliance and security management platform.
Traditional voice-specific threats are still a risk, such as toll fraud and session initiation protocol registration attacks, Lazar said. For example, callbacks are when a user receives a call that drops after one ring. Lazar said one out of 100 people will call back, which enables the original call to route somewhere where telco costs are expensive for the user, such as an international call.
Organizations need to create a strategy for implementing common security policies across collaboration apps, Lazar said. For example, if an organization uses both Microsoft Teams and Zoom, it needs a consistent set of policies on archiving chats, how files or data can be shared and limiting what users can and can't do.
Because collaboration platforms can be used for multiple modes of communications, organizations need to have consistency across all their tools, Redmond said.
Securing the home network
Organizations also need to consider where users are accessing collaboration platforms. Most remote employees will connect to corporate apps and the network through a VPN. This prevents unauthorized users from accessing the employee's network.
"The VPN tends to be the most successful approach," Lazar said. But VPNs don't work as effectively when accessing cloud apps like Zoom, he said. To address this, organizations can use a split tunnel approach.
A split tunnel enables employees to access corporate apps residing in the company data center through a VPN, while using their internet connection to access cloud-based apps. However, the tradeoff with split tunnels is that home internet connections are difficult for IT to control.
Organizations are increasingly considering Secure Access Service Edge (SASE) to address the challenge of home-based users and network security, Lazar said. SASE takes a zero-trust approach to security, where users can only see and access what the organization allows. Other components of SASE, such as secure web gateways and cloud access security brokers, also help secure network traffic and user endpoints.
UC and third-party vendors address security
UC vendors are seeing security as a differentiator for their services, Lazar said. After high-profile security issues during the pandemic, vendors have started to introduce capabilities like end-to-end encryption and user-controlled encryption keys.
Cisco, for example, has started to unify its network app security capabilities with UC security in a single dashboard for antivirus and malware protection that stretches across network and collaboration apps, Lazar said.
A third-party security platform can enable companies to set compliance and security policies across different platforms. More than half of organizations are using or planning to use a collaboration security platform, he said.
Third-party vendors vary in their security specialties. Some vendors, like Oracle and Ribbon, focus on voice security, while others, like SafeGuard Cyber and Theta Lake, focus on collaboration platforms.
A third-party platform like Theta Lake is designed to give organizations visibility across all tools as managing collaboration tools individually would make it difficult to enforce consistency, Redmond said.
"Collaboration tools are not going away," he said. "Thinking about how that changes the workplace around things like security and compliance needs to be a conversation at the top level for most organizations."






