session border controller (SBC)
What is a session border controller (SBC)?
A session border controller (SBC) is a dedicated hardware device or software application that governs the manner in which phone calls are initiated, conducted and terminated on a voice over Internet Protocol (VoIP) network. Phone calls are referred to as sessions.
An SBC acts as a router between a network and carrier service, enabling only authorized sessions to pass through the connection point or border. An SBC defines and monitors the quality of service (QoS) status for all sessions, ensuring that callers can actually communicate with each other and that emergency calls are delivered correctly and prioritized above all other calls. An SBC can also serve as a firewall for session traffic, applying its own QoS rules and identifying specific incoming threats to the communications environment.
For security reasons, session border controllers are likely to be deployed on both the carrier and enterprise sides of the connection. An SBC on the corporate network side is referred to as an enterprise SBC (E-SBC).
Functions of an SBC
SBCs control the admission of calls in and out of the networks. They often provide measurement, access control and data conversion for calls. SBCs modify the stream of call signaling data in each call, as well as redirect media traffic. They enable interoperability -- or the exchange and use of information between software -- by assimilating different signaling stream headers and messages. This enables systems that use different protocols to communicate with each other. Connections between different voice and video codecs can be translated as well.
SBCs also protect Session Initiation Protocol (SIP), which is used in VoIP networks. SIP is also one of the most important parts of any implementation for traditional service providers. It is a bedrock standard that governs how devices communicate over the internet.
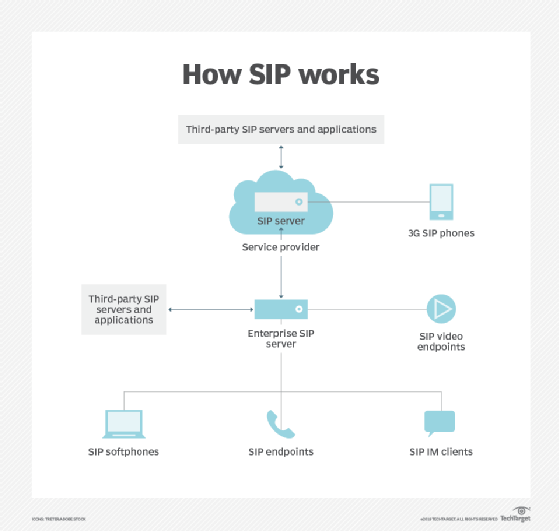
General functions of SBCs include the following:
- Security. SBCs monitor traffic and maintain security. They can be used to protect against both denial-of-service attacks and distributed DoS (DDoS) attacks. They can also provide other security measures, such as media and signaling encryption.
- Interworking protocols. SBCs enable different protocols to be translated between each other. For example, protocol translations among SIP, H.323 and SIP with encapsulated Integrated Services Digital Network User Part, or SIP-I, are possible.
- QoS. To provide QoS, SBCs enforce call admission control policies and rate limiting.
- Connectivity. SBCs works with IPv4 and IPv6 internetworking, virtual private networks and network address translation.
- Media services. SBCs provide digital signal processors, which enable border-based media control services, like media transcoding, data interworking and dual-tone multifrequency relay interworking.
Benefits of an SBC
SBCs offer organizations the following advantages:
- Security. An SBC's ability to monitor traffic enables it to protect against threats like DDoS attacks. Other actions, such as continual patches, also help provide an extra layer of security.
- Mitigation. SBCs can use pattern recognition to flag any unusual activity. This can help detect issues or attacks.
- Connectivity. Connectivity is more stable because multiple protocols can communicate with each other. Phone traffic is routed through internal IP networks, meaning calls are routed faster.
- Reliability. Normalization of SIP types helps ensure calls connect without interruption.
Examples of session border controller applications
Some examples of SBC applications include the following:
- AudioCodes Mediant E-SBC. This tool is based on the Mediant hybrid platform. It enables connectivity between time-division multiplexing and VoIP networks. It has a high call volume capacity with low rack space requirements.
- Avaya Aura Platform. This SBC provides a performance management module that can capture, analyze and store consumer interactions. This helps determine areas that may need improvement.
- Cisco Unified Border Element. This SBC-enabled router works with all SIP providers. It connects VoIP networks to each other and enables enterprise networks to connect internet telephony service provider networks.
- Oracle E-SBC. This SBC is intended for enterprise VoIP and unified communications networks. Microsoft has certified Oracle E-SBC for integration with Microsoft Teams.
Learn more about the role SBCs play in VoIP security in this article.







