Session Initiation Protocol (SIP)
What is Session Initiation Protocol (SIP)?
Session Initiation Protocol (SIP) is a signaling protocol used for initiating, maintaining, modifying and terminating real-time communications sessions between Internet Protocol (IP) devices. SIP enables voice, messaging, video and other communications applications and services between two or more endpoints on IP networks.
SIP was developed by the Internet Engineering Task Force in 1996 and standardized in 1999.
SIP addresses the evolving needs of IP-based communications. Native support for mobility, interoperability and multimedia was among the drivers behind SIP development. SIP complements other communications protocols, such as Real-Time Transport Protocol (RTP) and Real-Time Streaming Protocol, used in IP-based sessions.
SIP features
The SIP communications protocol determines five attributes when establishing and terminating multimedia sessions:
- user location
- user availability
- user capabilities
- session setup
- session management
SIP sessions can include internet telephony, video conferencing and other forms of unified communications. The protocol can be used to invite participants to unicast or Multicast sessions that do not necessarily involve the initiator.
SIP does not provide communication services. Instead, it defines interoperable implementations of SIP features, called primitives, which are used to facilitate different services. Primitives enable additional information to be embedded in a SIP message, such as linking a user's photo to directory information to enhance the user's caller ID.
SIP also supports name mapping and redirection services, which are two ways the protocol enables mobility. Users and endpoints are detected with a single identifier, or Uniform Resource Identifier (URI), which is independent of their network location. URIs are alphanumeric, using a syntax that looks more like an email address than a phone number or IP address. Other SIP features are available through application programming interfaces.
In addition to real-time services, SIP is used for asynchronous event notifications, such as automatic callbacks, message-waiting indicators and buddy lists based on presence.
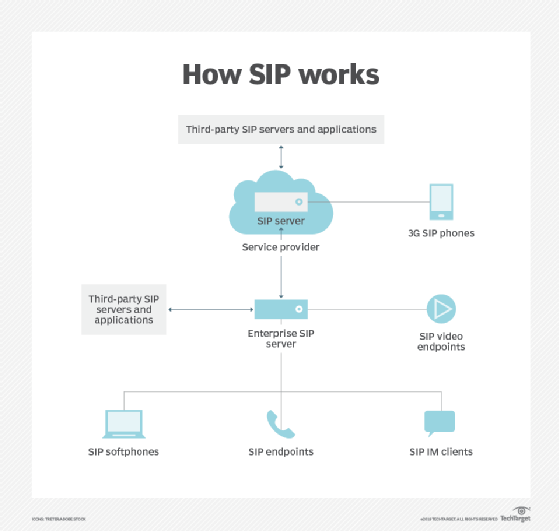
How does SIP protocol work?
SIP operates similarly to, and incorporates parts of, Hypertext Transfer Protocol (HTTP) and Simple Mail Transfer Protocol (SMTP). Like HTTP or SMTP, SIP works in the application layer of the Open Systems Interconnection communications model. It is supported by IPv4 and IPv6.
SIP can be thought of as a client-server architecture. SIP will also work in tandem with other protocols, namely Session Description Protocol (SDP), which is contained in SIP messages. SDP is used to describe multimedia communication to sessions for invitations, announcements and parameter negotiations.
Also, SIP is a text-based protocol, like HTTP, which means its content is in a readable format. This makes SIP easier to read and debug compared with similar signaling protocols, like H.323.
SIP is a request-response protocol. Requests and responses are the names message protocols send between devices to communicate. SIP receives requests from clients and responses from servers. Requests can be sent through any transport protocol, such as User Datagram Protocol, Stream Control Transmission Protocol or Transmission Control Protocol.
Devices using SIP communicate with each other directly via a SIP proxy server. The proxy acts as an intermediary system to offload tasks that would otherwise be handled by SIP.
SIP determines the endpoint used for a session, the communication media and media parameters, and whether the called party agrees to communicate. Then, SIP establishes call parameters at either end of the communication, also handling call transfer and termination.
Examples of SIP requests
SIP makes requests based on its features and functions. Here are examples of simple requests:
- Invite. Starts a dialogue that will initiate a call.
- . Confirms the other user has responded to a request.
- Update. Can be used to modify a session without changing the dialogue's state.
- Cancel. Stops pending requests.
- Bye. Ends dialogues and calls.
SIP and VoIP
In telecommunications, there are two phases to a voice call: the call setup and data transfer. Voice over IP (VoIP) is used to transmit voice and multimedia content over the internet. SIP can be thought of as the telephone switchboard operator in this process. It handles the call setup phase of VoIP calls.
The call setup part of the process involves organizing the details that get two phones or devices to connect. The data transfer takes place after the call setup. Protocols such as RTP send packets in the data transfer phase of a call.
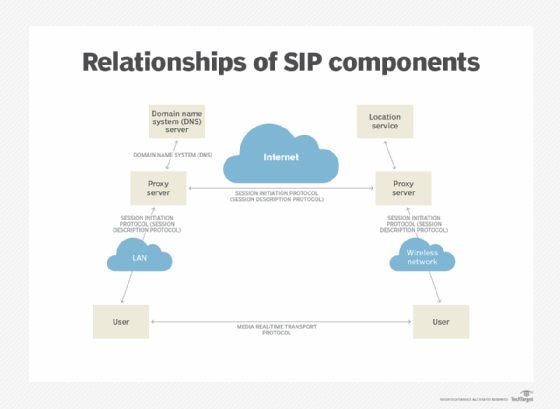
SIP networks consist of multiple elements that manage SIP requests between two endpoints. These elements are needed to set up a VoIP call, to make each endpoint aware of the other's IP address and to begin exchanging data.
The following are three main SIP network elements:
- User agents. These are endpoints or devices that can be clients or callers and servers or receivers.
- Registrar services. Also called a domain name systems in this case, they store information about the user agents -- such as the network/IP address -- in a database. They authenticate users in the network.
- Location services. These receive invite requests from the calling user. They query the registry for the call recipient's IP address and send the invite to the recipient user agent. The recipient's responses to the invite are sent back through the location server.
The location service and registrar service can be hosted together on one single server, known as the proxy server. The proxy server enables the registrar and location servers to perform the joint task of user authentication and provides the necessary information to communicate. They can also be hosted on their own independent servers.
While VoIP only deals with voice communication, SIP can handle other media transfer, such as images and video. Also, SIP is a protocol, whereas VoIP is a collection of technologies and methods that enable internet telephony. Many organizations use a technique called SIP trunking to improve VoIP efficiency in the enterprise.
SIP is now the standard for initiating IP network communication. Learn more about how SIP works and SIP trunking in this primer.







