The enterprise guide to video conferencing
The video conferencing guide helps enterprises navigate collaboration in a hybrid work environment and includes best practices for implementation and user training.
Video conferencing is in an incredible period of transition. Costly and complex in-room systems were the primary business investment before the pandemic. Those are now taking a backseat to individual video conferencing setups and plug-and-play office systems that create parity between in-room and remote experiences. This guide helps businesses understand the role video conferencing can play in hybrid work environments, including the benefits and challenges of video conferencing technology, game-changing features, bandwidth and security considerations, user best practices and more.
Why video conferencing is important for businesses
Video conferencing played a critical role during the height of the pandemic, enabling businesses to have employees work remotely but still stay connected. Now employers are entering a new era where video conferencing serves as a hub for hybrid work environments. Planning for such an environment, with users in the office a few days and remote (at home or elsewhere) a few days, carries different considerations than for an all-remote workforce. What remains constant, however, is the critical need for video conferencing platforms to be available and reliable as an essential communication and collaboration tool, as well as an integral part of the business workflow.
How has video conferencing evolved?
Video conferencing is a live, visual connection between two or more remote parties over the internet that simulates a face-to-face meeting. It is a core component of unified communications (UC) platforms and can be deployed as hardware, software or SaaS. Video conferencing's history stretches as far back as the 1870s when Bell Labs came up with the concept of transmitting an image and audio over wire. Decades later, in the 1920s, Bell Telephone Laboratories broadcast a live moving image. In the late 1990s, consumer webcams first became popular. But it wasn't until the early 2000s and the general availability of broadband that companies widely adopted video conferencing systems. Today, companies rely heavily on SaaS and web-based video conferencing platforms such as Webex by Cisco, Google Meet, Microsoft Teams and Zoom for collaboration, communication and presentations. Far from worrying about whether users will take to video conferencing, the technology is now so ubiquitous that businesses have to worry about issues such as video meeting fatigue, colloquially known as Zoom fatigue.
Business benefits of video conferencing
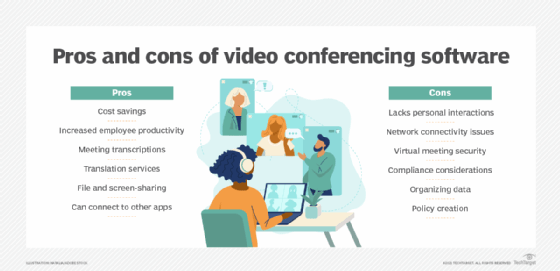
Video conferencing has many benefits in the business world, including a tremendous productivity boost. Users can reach out to colleagues in a meaningful way -- and while video conferencing technology doesn't replace in-person connections that can happen in an office, it is a worthy approximation.
Video conferencing supports the following: interpersonal communication, collaboration, and presentations and education.
Tasks such as recruiting, training, project management, collaboration with customers, and sales presentations and negotiations all benefit from an enterprise-level video conferencing platform.
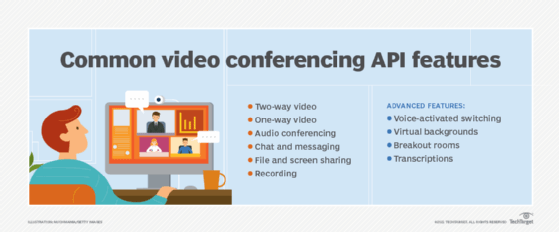
Features and capabilities of video conferencing technology
Video conferencing has matured over the past few years to include the following features that appeal to business users:
- Virtual backgrounds help avoid the distraction of a messy room or a user's remote location. Companies can create branded backgrounds to give video conferencing sessions a more professional look and feel.
- Screen-sharing makes it easy for participants to present or explain content in a clear manner. Some applications, such as Zoom, even have the capability of sharing a presentation as background so it feels more like an in-person experience.
- Together mode is an alternative to Gallery View that Microsoft released to enable Teams participants to appear in one screen together, as an audience rather than in individual boxes.
- Meeting transcription services track action items, next steps and other important session notes.
- Translation services enable meeting attendees to communicate in multiple languages and receive real-time transcripts.
- A gateway to other apps prevents users from having to launch and toggle among multiple programs.
While some platforms offer these features natively, third-party software is available to customize sessions on the fly, such as the open source Open Broadcaster Software.
Video conferencing also stands to benefit from AI and machine learning. IT leaders are already taking to AI-powered capabilities, such as automated transcription, facial recognition for starting meetings and voice recognition for controlling meetings.
Metrigy Research co-founder Irwin Lazar said AI could help address issues that will arise in hybrid work environments where some participants attend remotely and others are gathered in a room. For instance, AI could do the following:
- support active participant framing and picture quality improvement;
- increase active noise cancellation and acoustic fencing to filter out noise from pets, cars and the like;
- take real-time translation a step further with closed captioning;
- use facial recognition to identify speakers, then offer more information about them in real time to participants; and
- deploy chatbots to automatically schedule next meetings based on participant calendars.
With AI, businesses could better understand how employees and customers are using their video conferencing platforms, if the experience is effective and then adjust their strategy accordingly.
Editor Sandra Gittlen and Let's Do Video founder David Maldow discuss in-depth the pandemic's impact on video conferencing and how companies can best support users as they return to a hybrid work environment.
Challenges of video conferencing adoption
With all its benefits, video conferencing does have some challenges, with the greatest being how to make sure the user experience is the same whether an employee is in the office or remote. As Metrigy's Lazar said, "Anything that starts to complicate the meeting experience is not going to get a lot of traction."
From the user perspective, the video conferencing platform must be easy to navigate and have a similar look and feel no matter how or where the platform is accessed.
Bandwidth can be another significant challenge -- especially if users are largely remote and don't have access to high-speed connections. IT leaders must take the time to understand the bandwidth requirements for their preferred video conferencing platforms, including the demands of high-quality video. If users encounter significant latency, they will get frustrated and abandon the platform. Follow these step-by-step tips to calculate video conferencing bandwidth requirements for in-office and remote users.
How to handle video conferencing at the office is another challenge. Fixed in-room systems might be too expensive and complex to appeal to users who expect ease of use, mobility and agility from their video conferencing platforms. Those systems also tend to require a designated audiovisual tech to assist with meeting setup. Now vendors offer a range of plug-and-play systems that are more mobile and have features that help in-person and remote participants have a shared experience. For example, some software frames each attendee in the room as an individual, as it would remote attendees.
Archiving, storing and managing the files generated from video conferencing can be a headache, especially when a business is in a highly regulated industry, such as finance or health care. For example, regulations may require that IT log and preserve video and audio files as well as chat discussions and file sharing that might have occurred throughout the conference call.
Security and video conferencing
Security is a serious concern in video conferencing, especially as use cases for the technology increase. Telehealth is now a popular application for video conferencing platforms, but privacy regulations dictate how the platforms can be used, including what features can be turned on and who can use them.
Companies must make sure that the devices used to access the video conferencing platform are properly provisioned and secured, and that monitoring tools are in place to take notice of any security anomalies.
Security expert Ashwin Krishnan offered these 11 video conferencing security best practices:
- enforce starting rights for meetings;
- enable the waiting room and verify attendees;
- don't reuse meeting IDs;
- add a meeting password;
- lock the meeting once quorum is reached;
- remind attendees if a meeting is being recorded;
- use a virtual background;
- treat the chatroom with caution;
- keep software up to date;
- use encryption; and
- disable unneeded features.

Different categories of video conferencing
When selecting a video conferencing approach, it's important to know how the technology is going to be used. If use will be primarily in a boardroom or meeting room, then traditional hardware appliance-based solutions might still work best. Otherwise, consider using the personal-use video conferencing category.
Personal-use video conferencing can occur with a dedicated desktop appliance, be built into a desk phone, or be a software-based video conferencing (a.k.a. web conferencing) product that uses a desktop or mobile device camera.
Meeting rooms can be outfitted with personal-use video conferencing using a dedicated appliance; kits that combine a camera, compute and audio devices; or a laptop that can connect to the video conferencing platform.
It's also important to know the various video conferencing application deployment models: on premises, SaaS and hybrid cloud.
IT must decide if video conferencing is going to be standalone or integrated into a UC platform with other capabilities, such as voice over IP and webinar software.
Video conferencing software and vendors
There is no shortage of enterprise-class video conferencing vendors, including Avaya, Cisco, Fuze, Lifesize, Microsoft, Mitel, Poly, RingCentral and Zoom.
The type of architecture model a business wants to implement will help determine which vendors to pursue. Businesses also must decide if they want their platform to come from a multipurpose-vendor or single-purpose vendor.
Businesses should evaluate their vendors based on the following criteria: geographic location of the business's end users; migration path from a legacy video conferencing platform; integrations with same-vendor and third-party services; pricing and licensing model; and technical support options. As an example, Andrew Froehlich, president of West Gate Networks, provided this comparison of Microsoft Teams vs. Zoom.
Implementation of video conferencing
Implementing video conferencing technology is easy in some ways and difficult in others. For instance, writing code from scratch to add video capabilities to an application is "a herculean task", according to Let's Do Video's Maldow.
He recommended offloading some of the functionality to other services via an API. The results are faster development time, cost savings and updated features.
Maldow explained some of the features that APIs can enable, including virtual backgrounds, and best practices for selecting an API vendor.
Endpoints are another critical aspect of video conferencing implementation that should not be overlooked. Businesses should consider three factors when evaluating endpoints: how often employees use video; their role in the company, such as if they are customer-facing; and how the endpoints are funded.
Each organization implements video conferencing differently based on its users' needs, especially in a hybrid work environment. Editor Alissa Irei gathered the following five tips to improve hybrid video meetings:
- Add video capabilities to conference rooms.
- Consider virtual whiteboards.
- Upgrade video call quality with third-party gear.
- Supplement remote connectivity as necessary.
- Establish cultural norms.
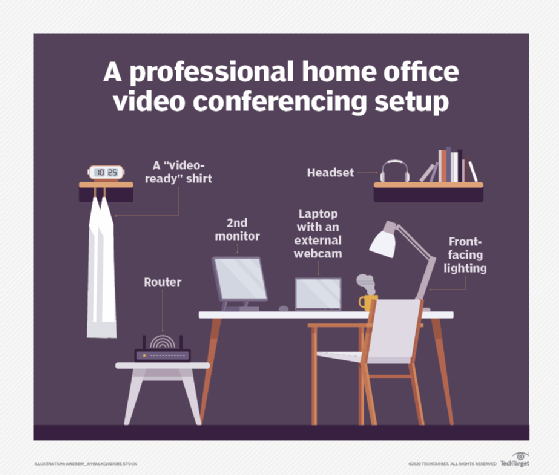
Video conferencing best practices for remote employees
Rolling out best practices to employees starts with achieving a professional home video conferencing setup.
Businesses with employees who are going to work remotely all or part of the time should assess their employees' home office environments and make adjustments that improve application performance, video quality and on-camera appearance and comfort.
This requires selecting the right gear with an eye to video and audio quality, high-speed connectivity and optimal workflow, which might require multiple monitors. Next, consider how the setup lights and frames the user. Some of this is taught, such as ideal camera angles, and some is bought, such as a ring light. Enterprises should help users understand the professional requirements of certain meetings, such as the use of branded virtual backgrounds, high-end external microphones and the proper way to use screen-share features.
In addition to home office best practices, companies should consider some basic meeting best practices to avoid burnout, including limiting meetings to less than an hour, reducing the overall number of meetings a user has to attend, resetting expectations about whether a participant needs to be on camera and avoiding back-to-back meetings with no breaks.
The use of video conferencing for businesses is in its prime right now, after being jumpstarted by pandemic-induced remote work. IT and users need to adapt to changing work environment to make the most of what is rapidly becoming an essential productivity and collaboration tool, whether employees are remote or in the office.